UPDATE: Unofficial patch available from Determina.
--------------------------------------------------------------
More stuff to worry about. This time a vulnerability again relating to Internet Explorer called [tag]setSlice()[/tag]. This relates to a flaw in webvw.dll. So far there's little in the way of info from Microsoft but there is a tool that has been developed by SANS that will disable it easily (download here).
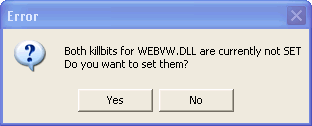
Killbit means making a change to the registry so that Internet Explorer cannot make use of this vulnerable DLL file.
For those in the know about killbits, here are the CLSIDs on which the killbit is being set:
- {844F4806-E8A8-11d2-9652-00C04FC30871}
- {E5DF9D10-3B52-11D1-83E8-00A0C90DC849}
It seems that this exploit is being used extensively by hackers:
And this is so massively exploited, it makes VML look cute. There’s a rootkit, some other malware, and haxdor! (a phishing trojan horse)
Here is all Microsoft has to say at present:
Microsoft is investigating new public reports of limited “zero-day” attacks using a vulnerability in Microsoft PowerPoint 2000, Microsoft PowerPoint 2002, Microsoft Office PowerPoint 2003, Microsoft PowerPoint 2004 for Mac, and Microsoft PowerPoint v. X for Mac.
In order for this attack to be carried out, a user must first open a malicious PowerPoint file attached to an e-mail or otherwise provided to them by an attacker.
As a best practice, users should always exercise extreme caution when opening unsolicited attachments from both known and unknown sources. Microsoft has added detection to the Windows Live OneCare safety scanner for up-to-date removal of malicious software that attempts to exploit this vulnerability.
Take care out there.
Like this:
Like Loading...







